What Two Functions Describe Uses of an Access Control List

In Today 39 S Highly Competitive Job Market Businesses Can 39 T Afford To Take A Lackluster Approach To Recruitment An Marketing Jobs Company Culture Hiring


Types Of Data Abstraction In Dbms Physical Logical View Data Link Layer Dbms Data Structures

What Is Access Control List Acl Types Linux Vs Windows Imperva
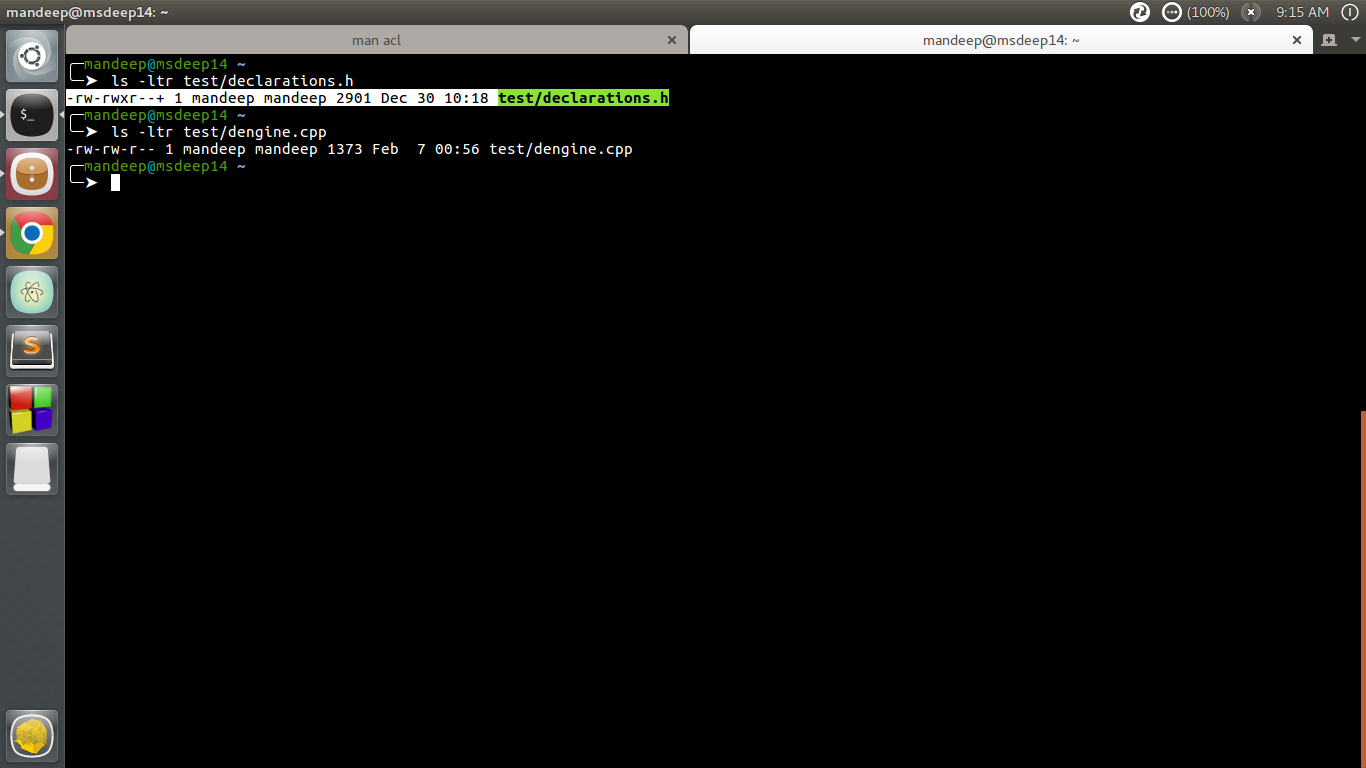
Access Control Lists Acl In Linux Geeksforgeeks
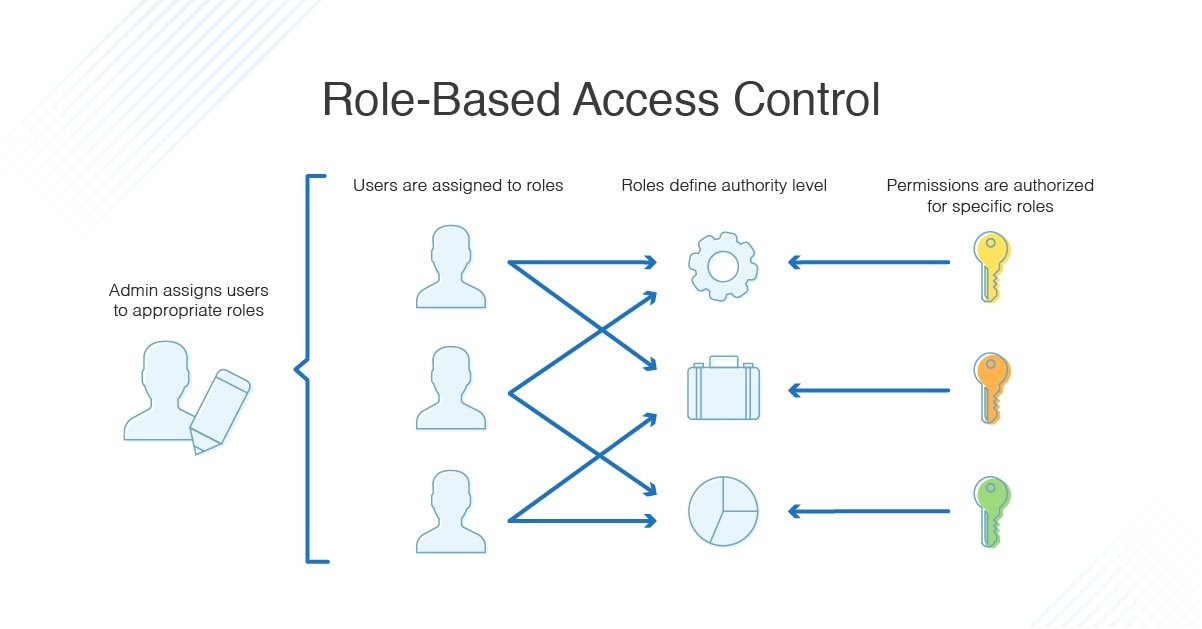
Rbac Vs Abac Access Control What S The Difference Dnsstuff

How To Use Aws Sam To Simplify Serverless Python Development Simplify Development Aws Serverless

Continual Service Improment Business Process Management Business Architecture Business Management

Python Decorators Explained A Step By Step Tutorial Learn To Code Python Learning

Cds Part 15 Associations In Cds Views I Sapspot Cds Data Services Meaningful Names

Fetch Decode Execute Cycle Worksheet Decoding Computer Architecture Teaching Resources

Principles Of Gis May 2019 Choice Based Question Paper Question Paper Management Information Systems Principles

Discover The Sixteen Personality Types Personalitopia Erik Thor Enfp Personality Intp Personality Type Introverted Sensing
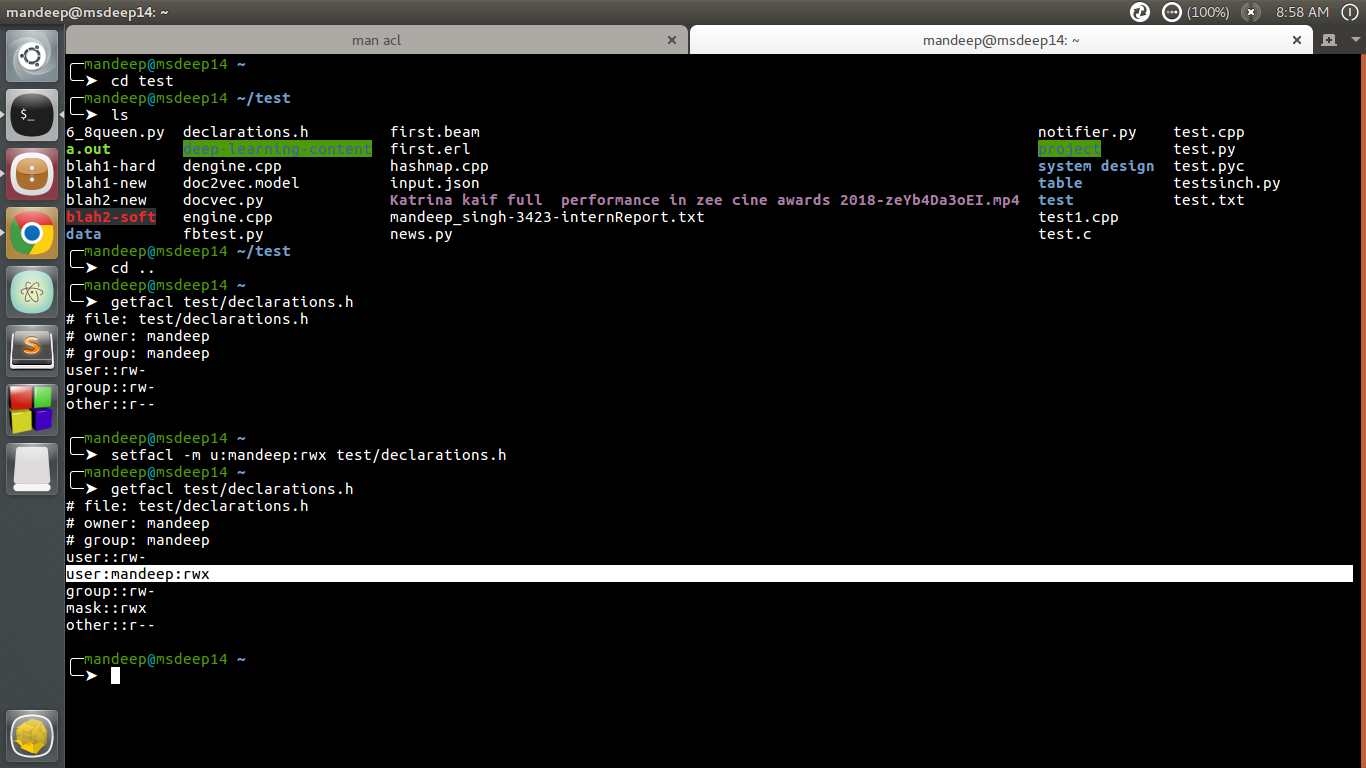
Access Control Lists Acl In Linux Geeksforgeeks

Oracle Database 12c Sql Fundamentals 1z0 061 Certification Exam Topics Album On Imgur Oracle Database Sql Exam

Ms Access Input Mask In Query Form Or Report Computer Help Internet Phone Access Database

The Open Business Data Lake Standard Business Data Master Data Management Information Governance

40 Quality Assurance Plan Template Hamiltonplastering Checklist Template Report Template Business Plan Template



Comments
Post a Comment